What is LINDDUN Threat Modeling
LINDDUN is a threat modeling method focused on privacy. It was developed by privacy experts at KU Leuven (a university in Leuven, Belgium). LINDDUN threat modeling identifies privacy threats and countermeasures and is able to do so early in the development process (much like other threat modeling methods).
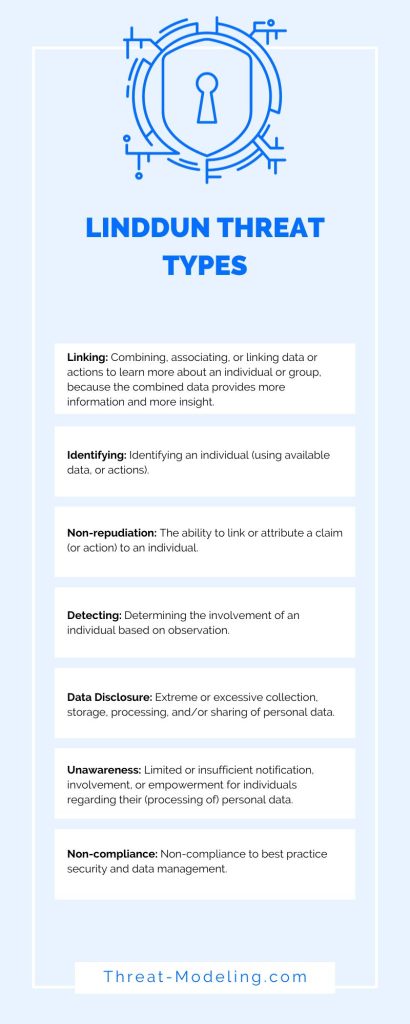
LINDDUN gets its name from Linking, Identifying, Non-repudiation, Detecting, Data Disclosure, Unawareness and Non-compliance. These are all privacy threat types.
LINDDUN focuses on privacy threats (and mitigations), whereas other common threat modeling methods, such as STRIDE and PASTA threat modeling, focus on security.
Key aspects of LINDDUN:
- Threat types: Privacy threat types help divide privacy concerns (much like STRIDE breaks down security concerns). There are seven threat types which spell LINDDUN.
- Threat trees: Privacy threat trees help to refine each of the seven threat types with more concrete characteristics, such as applicability and impact.
- Methods: There are three LINDDUN methods (Go, Pro, and Maestro). Go is the lighter version of LINDDUN, and PRO & Maestro are more systematic and exhaustive (more on this later in the article).
LINDDUN Threat Types
LINDDUN has seven privacy threat types: Linking, Identifying, Non-repudiation, Detecting, Data Disclosure, Unawareness and Non-compliance.
Linking: Combining, associating, or linking data or actions to learn more about an individual or group, because the combined data provides more information and more insight.
- Linking can occur with identifiers such as usernames, IP addresses, phone numbers, etc. By linking (or combining) these types of data, a bigger picture of the individual is developed. Further, profiling and other advanced methods can be used to link data together.
- Linking can be used on individuals and groups.
- Example Linking threats:
- A website combining actions from an anonymous user and based on those actions, the website manipulates offerings, reductions, etc.
- Combining a location data set, with a company’s data set, to infer which users work at which companies.
Identifying: Identifying an individual (using available data, or actions).
- Identification occurs when it is not possible to identify a person, yet by data leakage, deduction, or inference, it becomes possible.
- Identified data allows for direct linking of data to an identity. Identifiable data allows for indirect linking of data to an identity.
- Example Identifying threats:
- A website forces users to register with name and address, this allows the website to link all (previous and future) actions on the website to the name and address.
- An online forum links registered chats and posts (which have a user associated with them), with anonymous chats and posts by combining cookie data.
Non-repudiation: The ability to link or attribute a claim (or action) to an individual.
- It relates to the ability to attribute a claim or action to an individual. This prevents the ability of an individual to deny a claim or action.
- Non-repudiation is similar to the Repudiation threat in STRIDE. Although for security purposes, it is helpful to be able to link individuals to actions, whereas, for privacy purposes, it is helpful to not be able to link individuals to actions.
- Evidence used for repudiation includes logs, signatures, and metadata. This evidence links to individuals.
- Example non-repudiation threats:
- Having read receipts on messages, allows for confirmation that an individual has read a message.
- Health tracking data improves understanding of the personal health matters of an individual, which can be used against the same individual in insurance claims, or against legal accusations.
Detecting: Determining the involvement of an individual based on observation.
- It relates to inferring whether the mere existence of data proves something sensitive, rather than the contents of the data.
- Observed communications indicate communication between systems or people.
- Observed application side-effects indicate changes in a system from an application, such as memory usage, and temporary files.
- Evoked system responses indicate data through certain responses from a system.
- Example detecting threats:
- A deleted application from a computer or smartphone leaves behind data, indicating that the application once existed, with perhaps even contents of the application still available.
- Attempts to check whether certain users, or certain Email addresses exist within an application.
Data Disclosure: Extreme or excessive collection, storage, processing, and/or sharing of personal data.
- It relates to excessively collecting, storing, or processing personal data. Data should only be collected when it is absolutely required.
- There are four types of excessive data processing: unnecessary data types, excessive data volume, unnecessary processing, and excessive exposure.
- Example data disclosure threats:
- When a company collects data for its services within a web application, additional data is collected but not used. This additional data could be used for future sales purposes.
- Analytics tools on websites and web applications collect excessive amounts of data points.
Unawareness: Limited or insufficient notification, involvement, or empowerment for individuals regarding their (processing of) personal data.
- It relates to lack of transparency, lack of feedback and interminability.
- Lack of transparency means that a person is unaware of personal data collection and processing.
- Lack of feedback means that a person is not sufficiently informed of privacy impact.
- Lack of interminability means that a person cannot access or manage their personal data.
- Example unawareness threats:
- Users of an application are not informed of how their data is used, what data is collected, etc.
- Users of an application do not have access to their personal data and are not able to change it.
Non-compliance: Non-compliance to best practice security and data management.
- It relates to not upholding best practice security and data management.
- This can include unlawful processing of personal data, lack of data lifecycle management, or a lack of cybersecurity.
- Example non-compliance threats:
- Lack of security hardening of key components that make up an application.
- Collecting or using data clearly against GDPR, within the EU.
LINDDUN Threat Trees
LINDDUN threat trees help to zoom in, or zoom out, of LINDDUN threats. This helps users to look into threats at the right level of detail (from broad to in-depth).
There are seven threat trees, one for each threat type. Each tree varies in its detail between Tree Basic, Tree Examples, and Tree All Details.
Tree Basic only includes the high-level aspects of the threat type (for example Linking).
Tree Examples include the high-level aspects of the threat type and high-level examples.
Tree All Details includes the high-level aspects of the threat type and detailed examples
LINDDUN Methods
LINDDUN threat modeling has three methods to perform LINDDUN privacy threat modeling. They differ in how systematic and exhaustive the privacy threat modeling is required. The three methods are LINDDUN Go, LINDDUN Pro, and LINDDUN Maestro.
LINDDUN Go
LINDDUN Go is a lean (limited) approach aimed at teamwork. It is a game that can be played by a team (and thus improves teamwork and cooperation). The game forms a structured brainstorming session.
The lean approach helps to make LINDDUN approachable for teams and organizations that have limited time for privacy threat modeling.
LINDDUN Pro
LINDDUN Pro is a systematic approach to finding privacy issues. It includes the use of a Data Flow Diagram (DFD) (also used in other threat modeling methods such as STRIDE). It uses all the LINDDUN tools, which LINDDUN Go does not.
LINDDUN Maestro
LINDDUN Maestro is also a systematic approach to finding privacy issues (like LINDDUN Pro), however, it goes further in using an enriched (and more detailed) system description (rather than a more basic DFD).
What are the Steps in LINDDUN
The steps involved in LINDDUN threat modeling depend on the LINDDUN method (Go, Pro, or Maestro).
LINDDUN Go is a game, so has a gaming element to it with gaming steps. It is a card game (including 35 cards, each showing a threat) with rules to decide who does what (amongst the team members playing the game).
LINDDUN Pro has three high-level steps: 1) Model the system, 2) Elicit threats, and 3) Manage threats.
- Model the system: This step allows teams to understand what is being threat modeled. To achieve this, a Data Flow Diagram (DFD) is created, depicting external entities, data stores, processes, data flows, and trust zones.
- Elicit threats: This step consists of performing a systematic analysis of the system, with the aim of finding privacy threats. This is achieved by looking at each DFD interaction (data flows) and considering the privacy implications.
- Manage threats: Once threats are identified, they must be addressed and/or managed. The first step is to prioritize threats, the second step is to determine mitigation.
What is Privacy Threat Modeling
Privacy threat modeling is an activity to identify potential privacy threats in an application or system. By performing privacy threat modeling, it is possible to identify early on in a development process potential risks to privacy for various stakeholders.
Privacy threat modeling will identify privacy threats so that countermeasures can be developed before an application or system is in use.
Privacy threat modeling, such as LINDDUN threat modeling, allows you to systematically think about privacy threats, and the results can be used to demonstrate specific analysis and actions taken.


