You can perform threat modeling without any tooling whatsoever. In that case, all you need is motivation, a whiteboard (or a digital equivalent), good teamwork, and knowledge of threat modeling and threat modeling methods (e.g., STRIDE or PASTA). However, using a threat modeling tool can make the threat modeling process easier and more effective. Threat modeling tooling helps in a number of ways including:
- Following a specific and enforced process.
- Easier registration of results (i.e. threats and security requirements).
- Easier learning for new threat modelers.
- Getting automated input (for known threats and known threat intelligence sources).
- Better reporting (especially for enterprise environments).
- And more (see below for details).
I developed a tool to help with threat modeling, using the lessons learned of what makes great threat modeling possible.
Try the threat modeling tool. It’s completely free to use and doesn’t require a credit card. All you need to do is sign up.
If you’d like to try threat modeling with automation, please contact us!
Introducing the ‘Threat-Modeling.com’ Threat Modeling Tool
The threat-modeling.com tool is a powerful threat modeling tool that allows users to perform threat modeling easily and effectively.
It does so using two core techniques:
- Providing a powerful question/answer system highlighting key security concepts.
- Providing a diagramming solution to allow for the understanding of key components and information flows.
Want to start using the tool? click here for the (STRIDE / PASTA / generic) threat modeling tool!
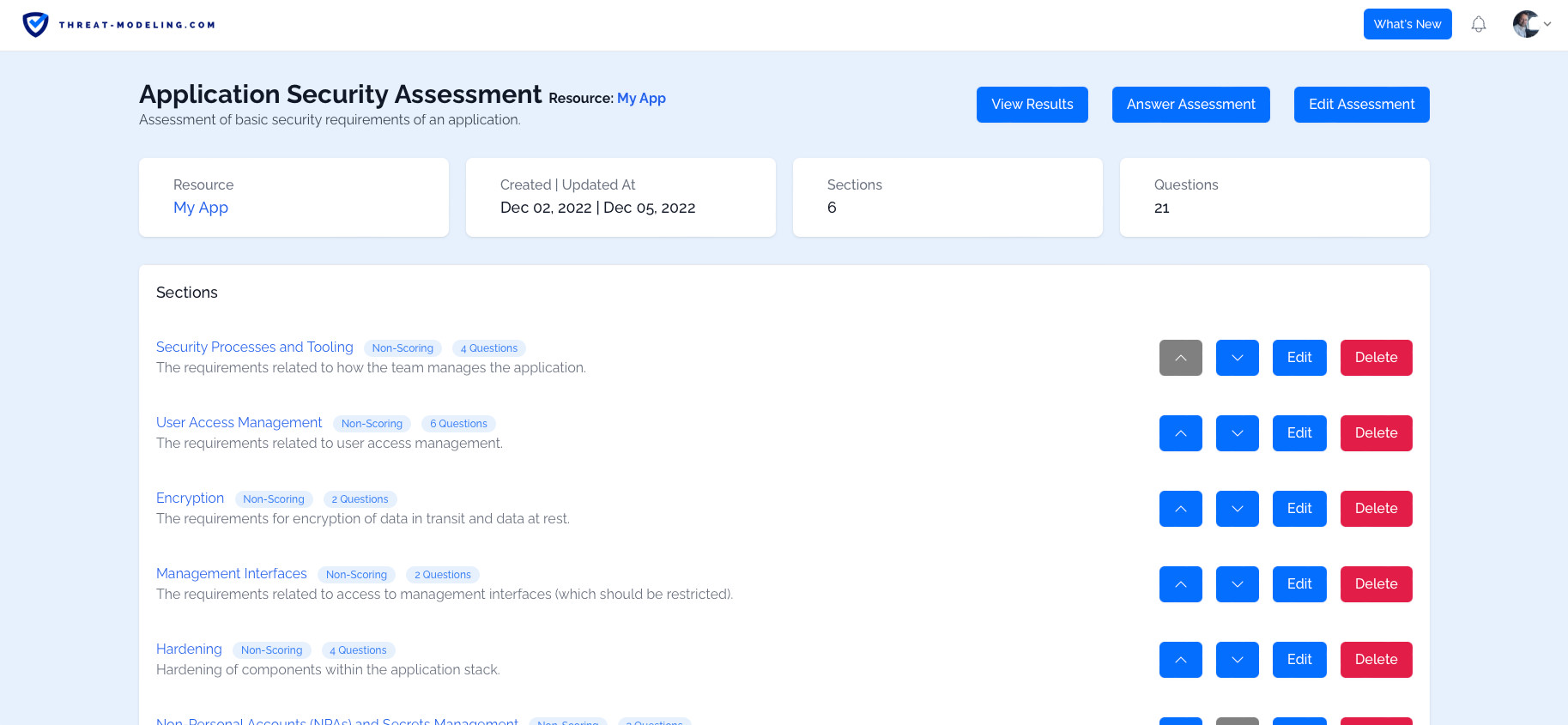
The image above shows an overview of the assessment feature of the threat modeling tool.
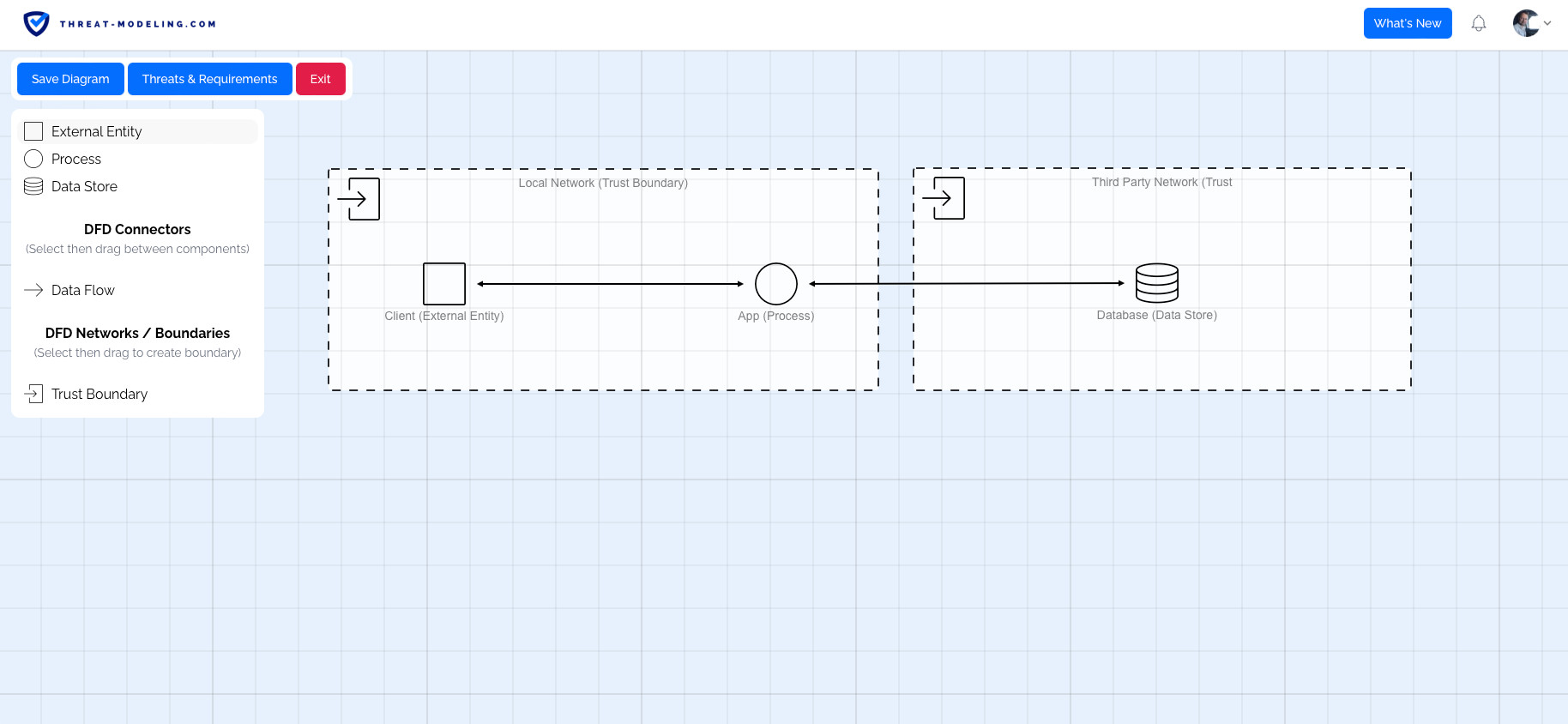
The image above shows the diagramming feature of the threat modeling tool.
Key Features of the Threat Modeling Tool
There are many features needed to provide an effective threat modeling tool. Below is an overview of the key features.
Note that new features and improvements are being made continuously.
Powerful Question and Answer System for Easy High Level Threat and Requirements Understanding
The tool allows you to create and use assessments. Assessments consist of questions that need to be answered. The questions are based on industry best practices and extensive threat modeling experience. The questions challenge users to think about security impact and potential security measures.
Based on the answers to questions, it’s possible to create threats and security requirements (see below for a description of threats and security requirements).
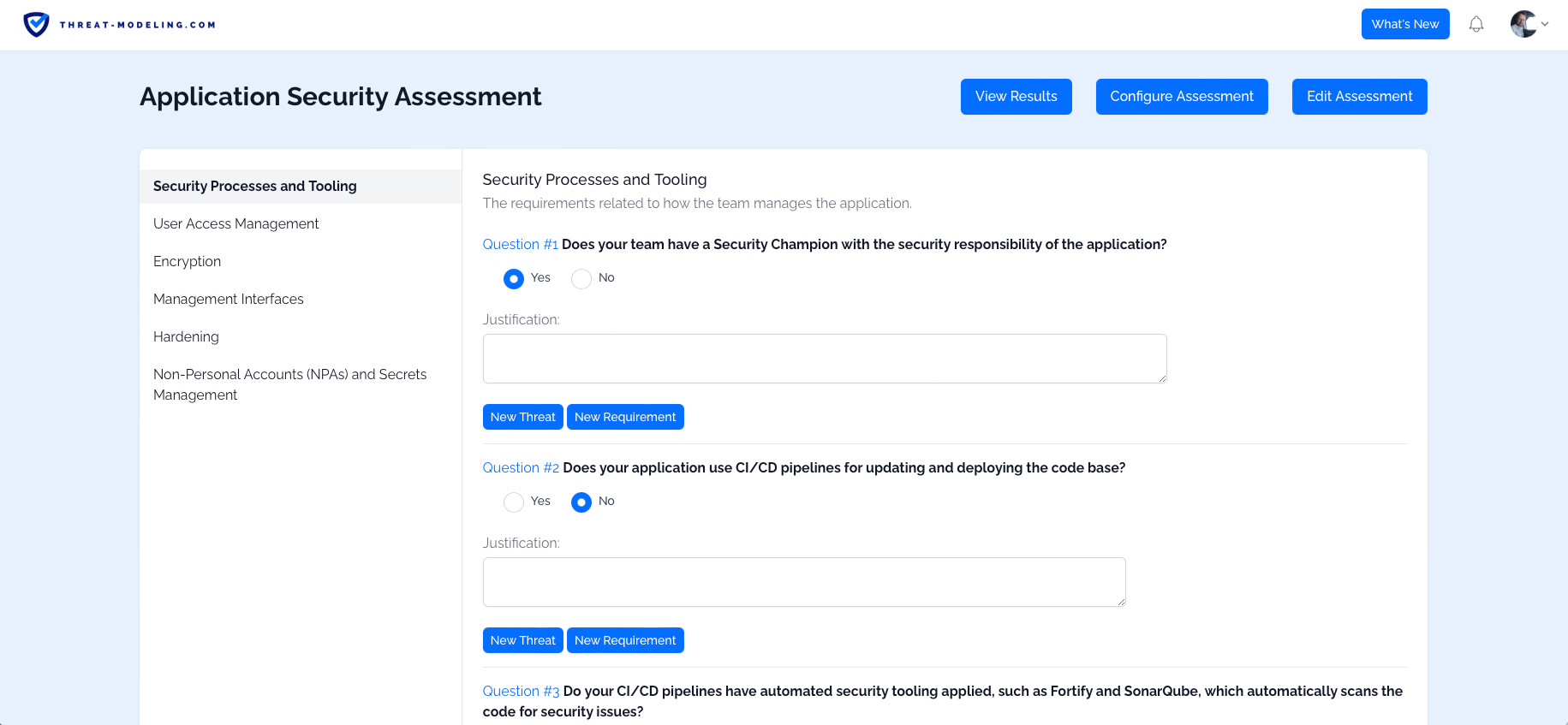
The image above shows questions that should be answered as part of the threat modeling process.
Easy and Insightful Diagramming for Component and Data Flow Understanding
The tool supports beautiful diagramming to create Data Flow Diagrams, and architectural diagrams for Azure, AWS, and other environments.
The diagrams help your team members to understand the main components used in a solution, communication flows, and more. This in turn allows team members to understand potential threats and develop security requirements.
Capture and Register Threats
The threat-modeling.com threat modeling tool allows threat modelers (your team members) to identify and register threats.
- Identifying threats: The tool helps users to identify potential threats, by asking ‘tough’ questions, and through the diagramming capabilities. Furthermore, there are repositories of common threats available.
- Registering threats: The tool allows users to save threats, which is helpful for tracking purposes. The threats are key to threat modeling, and key to creating countermeasures (in the form of security requirements).
Capture and Register Security Requirements
The ideal outcome of threat modeling is to identify and capture security requirements. Because, with security requirements, your team can develop a secure application or IT system.
The tool helps in identifying and creating security requirements. The security requirements can be created based on identified threats (as a countermeasure), or independently based on industry best practices, or from industry standards such as NIST, ISO27001, CAPEC, and OWASP (and its many projects).
Repository of Pre-Defined Threats and Security Requirements
The threat-modeling.com threat modeling tool has many pre-defined threats and security requirements.
How does that help? It provides you with industry best practices (from tried and true threat models, and solutions).
The sources of pre-defined threats and security requirements include NIST, ISO27001, CAPEC, and OWASP.
Easy Sign-Up and Usage
Easily sign-up and start using the tool. It’s free to sign up!
Using the tool is easy to learn. If you get stuck – there are plenty of learning materials available.
Granular User and Access Management
The tool has granular user and access management options ensuring that your threat model is only accessible to approved and authorized individuals. You are in control of your threat model.
Alternatives to the Threat-Modeling.com Tool
There are a number of alternatives to the threat modeling tool, including:
These are both powerful alternatives to the threat-modeling.com threat modeling tool.
Conclusion: Threat-Modeling.com Threat Modeling Tool is a Powerful Solution
Threat modeling is an effective way of identifying threats, and more importantly, to identify security requirements for your application or IT system.
However, performing threat modeling is not easy. The threat-modeling.com threat modeling tool helps you perform threat modeling without training, and without a background in (information) security.


