Attack trees threat modeling is a method that can be used for threat modeling. Attack trees can provide a helpful overview of potential attacks and attack types that can impact your threat modeling subject.
As the name would suggest, an attack tree is a tree of (potential) attacks divided in branches. It starts at a main or master node, and has branches from it. Branches can have multiple sub-branches. Each node/branch represents a (potential) attack.
An attack tree will tell you what can go wrong (which is one of Shostacks four questions). Each node represents one thing that can go wrong (which is an attack). Each node is related via branches, allowing for visual representation of connections or relations. This allows attack trees to show relations between attacks and attack types.
Attack trees can be used in cyber security as a general way of thinking about attacks, or it can be used as a tool or methodology within threat modeling.
Each node can hold additional data (on top of the attack or the attack type). For example, each node (an attack) could have additional information such as likelihood, prerequisites, threat actor, and more.
Attack trees are helpful in showing that there are many ways or methods that can be used to perform an attack. It broadens the thought process regarding potential attacks and attack types.
There are other threat modeling methods (or methodologies) that are helpful, and can be used in conjunction with attack trees:
Note that the threat modeling framework allows for using attack trees.
Why Use Attack Trees in Threat Modeling
Attack trees are a great way of understanding potential attacks (threats) to a system or process. Using attack trees has many advantages:
- Improves understanding of potential attacks.
- Visualizes relationships between attacks.
- Indicates how attacks, attack types and risk accumulates.
- Visually easy to understand making great to share with team members who will easily understand and consume it.
- Can be customized to your specific needs.
- Work well with DevOps teams and agile development environments.
How to Create an Attack Tree
An attack tree consists of nodes and branches.
Each node is an ‘attack’ or a type of attack. An example of a node (an attack): “Gain access to an administrative panel”.
Each branch represents a relationship between nodes. The relationship can be solid or casual (that’s up to you as you create an attack tree). The branch information is typically limited so you have to see the nodes to figure out the relationship between them.
The main or master node identifies that overall attack or attack objective. These are typically higher level or more broad in nature. As the attack tree gains more nodes and branches, the nodes get more specific.
An attack tree should be started at the main or master node, and should subsequently drill down with sub-nodes and branches. All the sub-nodes and branches should support the main or master node.
Steps involved in attack trees threat modeling:
- Step 1: Create the main (or master) node. This is the overall attack that should be considered for the entire attack tree. It should be general enough to explore more specific underlying attacks.
- Step 2: Create a sub-node, which is a specific type of attack that supports the main node (and it’s most high-level attack). It should be connected via a branch.
- Step 3: Enter additional parameters that you’d like to document per node. For example, the likelihood, the impact, the prerequisites, etc.
- Repeat: Repeat step 3 until all relevant attacks and attack types have been identified.
- Step 4: Conclude the attack tree, noting the overall attacks applicable.
- Step 5: Create additional attack trees for other attack scenarios.
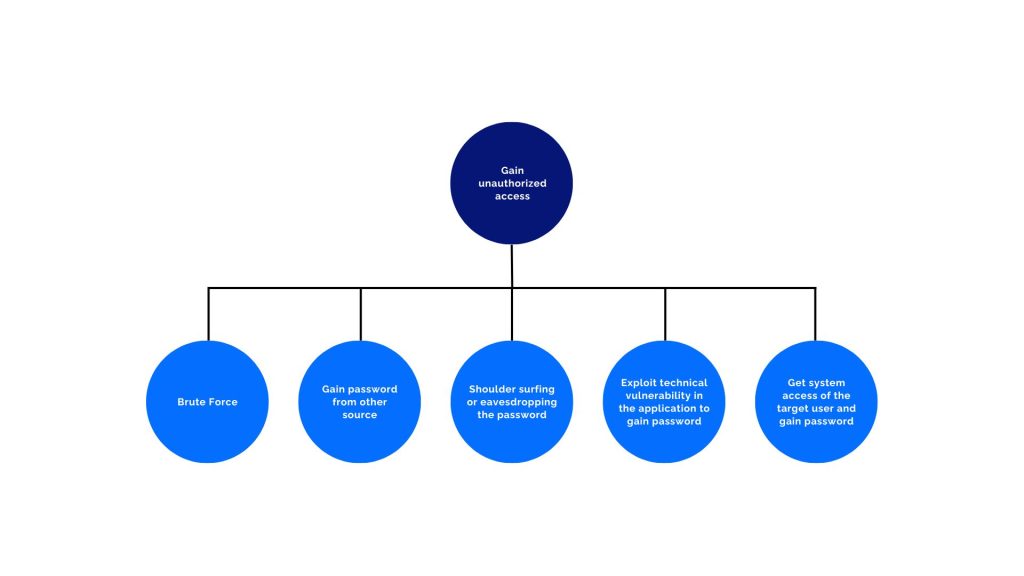
The image above shows a conceptual example of gaining unauthorized access to a system. Below the main node there are sub-nodes showing potential attacks.
Attack Trees Threat Modeling Conclusion
Attack trees threat modeling is an effective method of threat modeling. It can be used by both technical and non-technical team members.
It results in a diagram that can be easily understood. This means that teams will be able to consume an attack tree immediately, which in turn means that teams can work on next steps: remediating attacks and securing products and software.


