23andMe was attacked, or specifically, its users were, which resulted in a major data breach affecting many of its users (potentially up to 4 million users). The data breached relates to DNA testing results and additional ancestry analysis, which relate to the ‘DNA Relatives’ feature at 23andMe. The attacker posted some of the breached data on a public forum.
Sources:
Note: This threat modeling analysis is based on publicly available information. Publicly available information may differ from what actually occurred. Further, new information may be disclosed as it is discovered and published.
The key takeaway: Organizations must protect users by enforcing strong authentication measures like multi-factor authentication (MFA), especially if confidential data is involved, and even if it adds friction to the user experience.
Background
23andMe is a DNA testing service that allows users to analyze their DNA. Using the DNA data, 23andMe can analyze potential relatives and information about their ancestry. For example, whether a user is from a specific part of the world, the makeup of their race and ethnicity, and whether there are relations known to 23andMe (e.g., brothers, sisters, etc.).
Threat Modeling Diagram and Key Components Involved
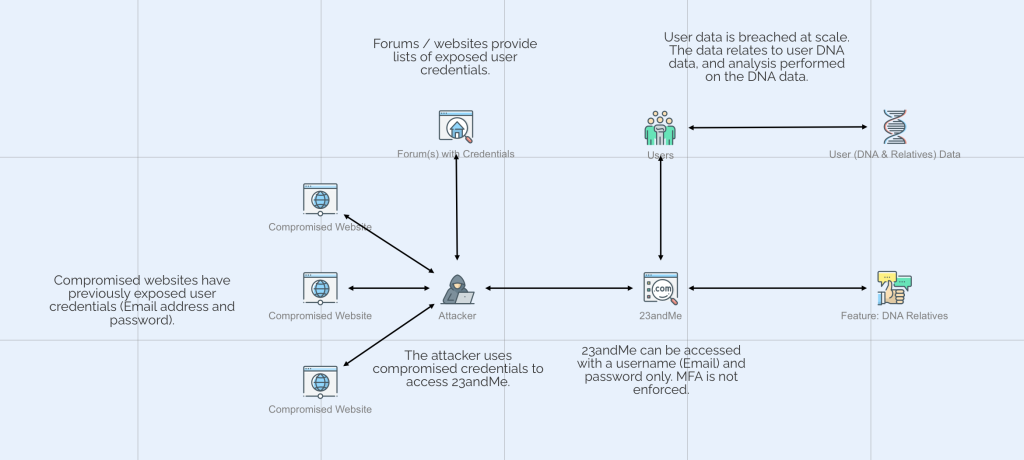
Key actors/components:
- Compromised websites: Websites previously compromised or breached, expose their users’ credentials. These same credentials are re-used on other websites including 23andMe.
- Forum(s) with Credentials: Forums and websites collect the compromised credentials so attackers can easily use them.
- Attacker: The attacker accesses 23andMe using the compromised credentials, this is possible because users re-use credentials (crucially their password) across websites.
- Users & User Data: The users’ data is compromised, consisting of DNA data.
- DNA Relatives Feature: This feature was abused during the attack. It connects data between users (e.g., highlighting family relationships).
The Threats (or Weaknesses) Exploited in the Data Breach
23andMe was not directly attacked, and its systems were not directly compromised.
Rather, the attack was directed at 23andMe users using credential stuffing. Attackers used user credentials (i.e., usernames and passwords) that have been compromised in other attacks to access 23andMe. Therefore, the affected users re-used passwords across websites including 23andMe.
Threats or weaknesses exploited:
- Users only use usernames and passwords for authentication (or something they ‘know’).
- Multi-factor authentication (MFA) is provided by 23andMe, but not enforced (presumably due to added user experience friction).
- Users are able to re-use breached usernames (Email addresses) and passwords from other websites.
Potential Countermeasures (or Security Requirements)
The following countermeasures or security requirements would (partially) mitigate the threat:
- Enforce the use of multi-factor authentication (MFA) by its users. This could add friction to using the service. Therefore, the MFA onboarding process must be quick and easy to use.
- If MFA cannot be enforced, strongly suggest and remind users that MFA should be used.
- Proactively scan for credentials that are used on 23andMe which are known to be breached on other websites, and enforce that the user cannot use vulnerable credentials. For example, haveibeenpwned provides a service to determine if credentials have been breached.
- Proactively monitor for suspicious login attempts at scale. For example, if thousands of logins occur from the same IP or login locations differ from known previous locations. This may be difficult to perform in practice.
The Threat Actor(s)
The threat actor (or attacker) has the following characteristics:
- External – No access to internal systems and no access to internal employees.
- Technically proficient – The threat actor was able to identify weaknesses in the authentication process and leverage compromised credentials.
- Motivated by money – The threat actor probably posted the breached data as proof of the breach, to request payment from 23andMe (this is not confirmed).