NIST Cyber Security Framework (CSF) 2.0 is a comprehensive framework that describes how cyber security should be organized and implemented to secure an organization from cyber risks. It is widely used and therefore a well-known standard within the industry. NIST CSF was initially released in 2014, and the NIST CSF 2.0 update was released in February 2024.
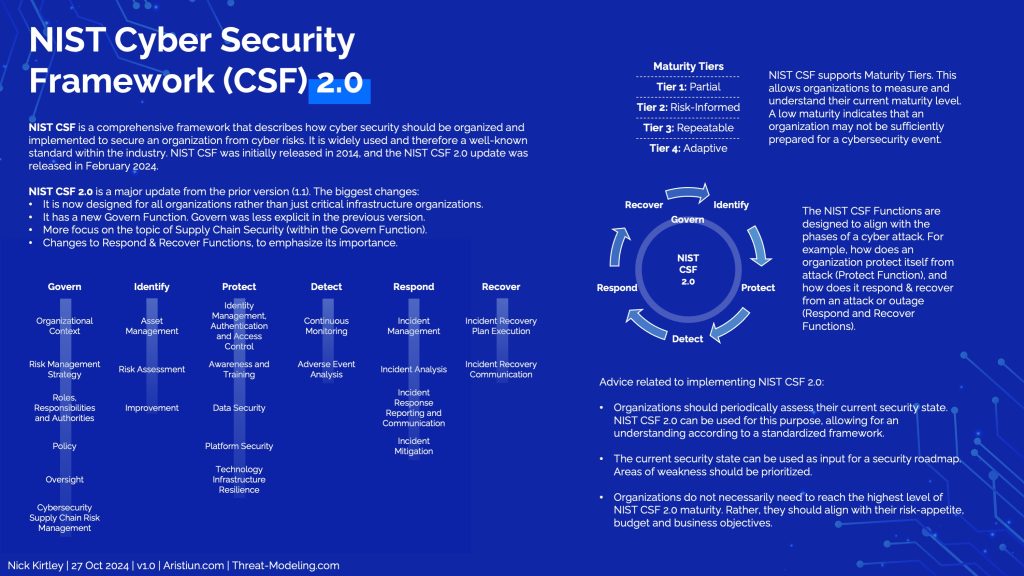
NIST CSF 2.0 is a major update from the prior version (1.1). The biggest changes:
- It is now designed for all organizations rather than just critical infrastructure organizations.
- It has a new Govern Function. Govern was less explicit in the previous version.
- More focus on the topic of Supply Chain Security (within the Govern Function).
- Changes to Respond & Recover Functions, to emphasize its importance.
Functions
NIST Functions:
- Govern: The organization’s cybersecurity risk management strategy, expectations, and policy are established, communicated, and monitored.
- Identify: The organization’s current cybersecurity risks are understood.
- Protect: Safeguards to manage the organization’s cybersecurity risks are used.
- Detect: Possible cybersecurity attacks and compromises are found and analyzed.
- Respond: Actions regarding a detected cybersecurity incident are taken.
- Recover: Assets and operations affected by a cybersecurity incident are restored.
The NIST CSF Functions are designed to align with the phases of a cyber attack. For example, how does an organization protect itself from attack (Protect Function), and how does it respond & recover from an attack or outage (Respond and Recover Functions).
Maturity Tiers
There are four tiers:
- Tier 1: Partial
- Risk Management Process: Organizational cybersecurity risk management practices are not formalized, and risk is managed in an ad hoc and sometimes reactive manner.
- Integrated Risk Management Program: There is limited awareness of cybersecurity risk at the organizational level. The organization implements cybersecurity risk management on an irregular, case-by-case basis due to varied experience or information gained from outside sources.
- External Participation: The organization does not understand its role in the larger ecosystem of its dependencies or dependents. The organization does not collaborate with or receive information (e.g.,
threat intelligence, best practices, technologies) from other entities (e.g., buyers, suppliers, dependencies, dependents, Information Sharing and Analysis Organizations, researchers, governments), nor does it share information.
- Tier 2: Risk-Informed
- Risk Management Process: Risk management practices are approved by management but may not be established organization-wide.
- Integrated Risk Management Program: There is an awareness of cybersecurity risk at the organizational level, but there is no established organization-wide approach to managing cybersecurity risk. Cybersecurity information is shared within the organization on an informal basis.
- External Participation: Generally, the organization understands its role in the larger ecosystem with respect to either its own dependencies or dependents, but not both. The organization collaborates with and receives some information from other entities and generates some of its own information but may not share information with others.
- Tier 3: Repeatable
- Risk Management Process: The organization’s risk management practices are formally approved and expressed as policy.
- Integrated Risk Management Program: There is an organization-wide approach to manage cybersecurity risk. Risk-informed policies, processes, and procedures are defined, implemented as
intended, and reviewed. - External Participation: The organization understands its role, dependencies, and dependents in the larger ecosystem and may contribute to the community’s broader understanding of risks. It
collaborates with and regularly receives information from other entities that complements internally generated information, and shares information with other entities.
- Tier 4: Adaptive
- Management Process: The organization adapts its cybersecurity practices based on previous and current cybersecurity activities, including lessons learned and predictive indicators.
- Integrated Risk Management Program: There is an organization-wide approach to managing cybersecurity risk that uses risk-informed policies, processes, and procedures to address potential cybersecurity events. The relationship between cybersecurity risk and organizational objectives is clearly understood and considered when making decisions.
- External Participation: The organization understands its role, dependencies, and dependents in the larger ecosystem and contributes to the community’s broader understanding of risks. It receives, generates, and reviews prioritized information that informs continuous analysis of its risks as the threat and technology landscapes evolve. The organization shares that information internally and externally with other collaborators.
NIST CSF supports Maturity Tiers. This allows organizations to measure and understand their current maturity level. A low maturity indicates that an organization may not be sufficiently prepared for a cybersecurity event.
NIST Cyber Security Framework (CSF) 2.0 Advice
Advice related to implementing NIST CSF 2.0:
- Organizations should periodically assess their current security state. NIST CSF 2.0 can be used for this purpose, allowing for an understanding according to a standardized framework.
- The current security state can be used as input for a security roadmap. Areas of weakness should be prioritized.
- Organizations do not necessarily need to reach the highest level of NIST CSF 2.0 maturity. Rather, they should align with their risk-appetite, budget and business objectives.


